Ten computer viruses that changed the world
In HackingBrain (1986)
It’s almost 25 years since the first PC computer virus left users looking at corrupted floppies, lost work and perplexing messages. In that time, the state of the art in automated malfeasance has progressed to the point that it’s part of the armory of international geopolitics. Stuxnet, while still mysterious, left nobody in any doubt that viruses and worms can be used in the highest-stake game there is.
Along the way, hundreds of millions of infections have taken place, billions of dollars have been lost in productivity and broken systems, and the anti-malware industry has grown to become a significant player in the IT market. It’s not over yet: perhaps it never will be, but the history of malware is a fascinating insight into the technology and culture of the digital world.
1. Brain (1986)
It sounded like science fiction, but it was all too real. Basit and Amjad Farooq Alvi, a pair of software programmers from Pakistan, became annoyed at people duplicating their products and created what was supposed to be a kill switch for illicit copies. But the design was flawed; the anti-copy software could duplicate itself — and did.
The first worldwide PC virus, Brain worked by changing the boot sector of a floppy. When an infected floppy was put into a computer, it installed Brain in the computer’s memory, from where it infected new floppies as they were inserted.
The brothers included their names, address and phone numbers in the virus, ostensibly to offer their services to decontaminate infected computers. They subsequently regretted this.
Christmas Tree (1987) A single design flaw can turn a harmless joke into a weapon. The Christmas Tree Exec was a script that ran under the Rexx language and did two simple things: it drew a Christmas tree, using text for graphics, and then sent a copy of itself to everyone in the target’s email contacts list.
A single design flaw can turn a harmless joke into a weapon. The Christmas Tree Exec was a script that ran under the Rexx language and did two simple things: it drew a Christmas tree, using text for graphics, and then sent a copy of itself to everyone in the target’s email contacts list.
The original started on Earn, the European Academic Research Network, and spread quickly to the US equivalent, Bitnet. The infection then hopped over to IBM’s internal VNET, where it took advantage of the IBM habit of having really large address books.
As the worm depended on running in an IBM mainframe environment, it didn’t spread beyond those networks. It lasted six days on Bitnet and only four on VNET, where it was finally removed by shutting down the entire network.
Morris worm (1988)
The first malware to be propagated widely via the internet, the Morris Worm or Great Worm hit around 6,000 of the 60,000 computers on the network in 1988.
Robert Morris (pictured), then a student at Cornell University, maintains that his worm wasn’t malicious, but was designed to measure the size of the internet. Others took a different view, as the worm used a batch of security flaws in Unix and was launched surreptitiously.
It was certainly unwelcome, as it was far more aggressive at making copies of itself than it needed to be, often infecting machines multiple times, turning what might have been an easily contained annoyance into a powerful denial-of-service attack. Morris became the first person to be convicted under the 1986 US Computer Fraud and Abuse Act, and the incident led to the formation of the first Computer Emergency Response Team Coordination Center, CERT/CC.
Melissa (1999) Named after a lapdancer and released in a document posted to the alt.sex Usenet newsgroup, Melissa had a salacious start in life. Users who opened the document, eager to read the 80 passwords to porn sites promised within, found that the document immediately forwarded itself to the first 50 people in their address book. Which could take a whole lot of ‘splainin.
Named after a lapdancer and released in a document posted to the alt.sex Usenet newsgroup, Melissa had a salacious start in life. Users who opened the document, eager to read the 80 passwords to porn sites promised within, found that the document immediately forwarded itself to the first 50 people in their address book. Which could take a whole lot of ‘splainin.
The virus created so much email that many companies had to turn off their internet gateway to regain control of their systems. As a result, the writer — a 30-year-old man called David Smith — got a 20-month prison sentence, despite helping the FBI track down and nab other virus writers.
ILOVEYOU (2000)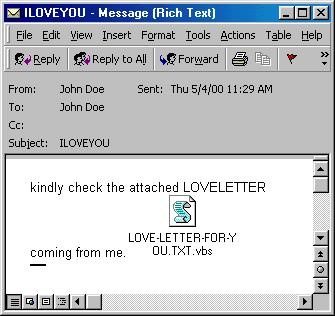 The ILOVEYOU worm was a devastatingly fast-spreading and effective combo of social engineering and Windows design flaw exploitation. The cost of clean-up and lost work due to the worm, also known as the Love Bug, is thought to total between $5bn and $10bn.
The ILOVEYOU worm was a devastatingly fast-spreading and effective combo of social engineering and Windows design flaw exploitation. The cost of clean-up and lost work due to the worm, also known as the Love Bug, is thought to total between $5bn and $10bn.
The worm was the work of two Filipino students who were caught, but the case was dropped because there was no applicable law at the time. ILOVEYOU used Microsoft’s Visual Basic Scripting (VBS) to forward itself to the contents of the host’s Outlook address book. It also overwrote files with copies of itself and tweaked the Windows registry.
It spread around 15 times faster than Melissa, according to the US Army. With at least 50 million computers infected and many large organisations having to shut off internet access, ILOVEYOU highlighted the vulnerabilities within Windows and sparked off large amounts of criticism and me-too infections.
Santy (2004) A specialized worm that demonstrated quite how subtle attack vectors could be, Santy used search engines — Google at first, then Yahoo and AOL — to find vulnerable sites running phpBB bulletin board software, which it then attacked. It spread worldwide in less than three hours.
A specialized worm that demonstrated quite how subtle attack vectors could be, Santy used search engines — Google at first, then Yahoo and AOL — to find vulnerable sites running phpBB bulletin board software, which it then attacked. It spread worldwide in less than three hours.
The most unusual aspect of the worm was that someone then produced an anti-Santy worm that used the same techniques to find and infect phpBB installations, but then patched the problem and inoculated the sites against further attack.
Conficker (2008)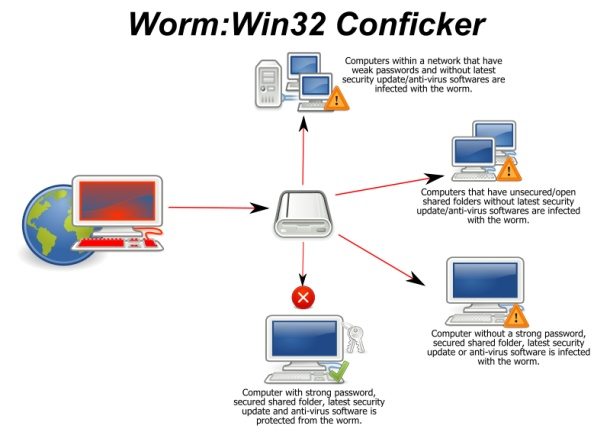 This Windows worm, also known as Downadup, hit up to 15 million Microsoft servers, causing operational problems for the British, German and French military among many others. Its use of encryption and stealth code hiding made it very difficult to eradicate, as have its constant revisions: it went through five major updates in six months.
This Windows worm, also known as Downadup, hit up to 15 million Microsoft servers, causing operational problems for the British, German and French military among many others. Its use of encryption and stealth code hiding made it very difficult to eradicate, as have its constant revisions: it went through five major updates in six months.
Those revisions have demonstrated that the Conficker writers are closely observing and reacting to industry efforts to eradicate the malware. In response, Microsoft convened a working group of companies across the internet and security markets, and put up a $250,000 bounty for information leading to the conviction of the miscreants.
Stuxnet (2010) The most sophisticated malware observed, this is a uniquely targeted worm that propagates via Windows and attacks industrial controller hardware — but only of a certain configuration (such as the Siemens S7-300 controller, above).
The most sophisticated malware observed, this is a uniquely targeted worm that propagates via Windows and attacks industrial controller hardware — but only of a certain configuration (such as the Siemens S7-300 controller, above).
It is thought to have been designed to damage the Iranian nuclear programme, and may well have succeeded. When it finds its target system, it reprograms high-frequency motor controllers to operate in an intermittently out-of-specification way. It thereby upsets industrial processes in a manner that’s hard to identify.
Although the authors of Stuxnet aren’t known, reports earlier this year said that the malware was claimed as a success of the Israeli Defence Force, in a video shown at the retirement party of the force’s chief of general staff, Lieutenant General Gabi Ashkenaz.

When HARLIE Was One by David Gerrold (1972)
The first fictional computer virus was written by an errant, intelligent, eponymous computer that wanted to gather information about its creator for blackmail purposes. Although the propagation method described in When HARLIE Was One was unusual, it was apt for a time before the internet took off:
“You have a computer with an auto-dial phone link. You put the VIRUS program in it and it starts dialling phone numbers at random until it connects to another computer with an auto-dial. The VIRUS program then injects itself into the new computer.”
The Shockwave Rider by John Brunner (1975) If HARLIE lived in a world without computer networking, The Shockwave Rider saw the network as the most important part of new technology and one that could massively affect human society — and thus qualifies as a genuinely visionary pre-internet SF novel.
If HARLIE lived in a world without computer networking, The Shockwave Rider saw the network as the most important part of new technology and one that could massively affect human society — and thus qualifies as a genuinely visionary pre-internet SF novel.
In the novel, worms and counter-worms are sent into the network to do battle by proxy on behalf of their writers; this often involves deception and identity theft. The nature of online identity, the role of online groups in shaping society, and the symbiosis between human and networks are all themes that bear examination more than 30 years on.